Data center security What is data center security?
Data security is the process of protecting digital data from unauthorized access, corruption, or theft that may occur from a breach in physical security, data breach, or cyberattack.
The growing wave of east-west data center (server-to-server) traffic is redefining security requirements. The speed and volume of east-west traffic in virtualized and containerized application environments require new security solutions, especially in multitenant scenarios where Zero Trust Security is imperative.
Table of Contents

Data Center Security and Zero Trust
The cybersecurity threat landscape has changed dramatically in recent years. Today, adversaries are more motivated than ever to penetrate enterprise data centers and steal valuable information. For the data center, this means trusting no entity on the network by default and distrusting all traffic unless a security policy explicitly allows it.
With microservices-based applications, traffic may never be inspected by a hardware firewall, IPS, or other security devices—leaving enterprises vulnerable to attack from within the enterprise itself.
According to NIST SP 800-207, “Zero-trust security models assume that an attacker is present in the environment” and that a Zero Trust architecture is “designed to prevent data breaches and limit internal lateral movement.”
The two biggest threats to data centers are:
- Infrastructure attacks: Enterprises depend on their technology assets to maintain operations, so protecting technology infrastructure protects the organization itself. Exploits against the functionality of data center components (storage, compute, and network) results in loss of performance, availability, proprietary data, and intellectual property (IP), negatively impacting company’s profitability.
- Cyberattacks: Threats to technology infrastructure range from phishing attempts and ransomware attacks to distributed denial of service (DDoS) exploits and Internet of Things (IoT) botnets. Dedicated security systems with advanced monitoring, application-aware policy enforcement, and threat detection ensure business-critical and customer-facing applications can run seamlessly.
Components of a secure data center
Modern data center security requires granular visibility, policy control, and automated threat detection and mitigation without added complexity.
1. Complete visibility
Data center networks change rapidly. The most pressing challenge is maintaining operational stability and visibility for users while moving or upgrading computing and storage resources.
Although telemetry from many types of security infrastructure can be aggregated, it is often time-consuming and identifies problems only after they have already occurred.
2. Segmentation
To properly define policy for which connections are permitted and which must be denied, it is necessary to understand the various user profiles associated with applications and data. By identifying requirements, appropriate data center access profiles can be developed accordingly. Segmentation is a logical separation of data center hosts between which a security policy can be enforced.
Segmentation prevents unwanted lateral movement by statefully inspecting all east-west traffic in the data center and applying policies that stop bad actors from moving through the internal network. Microsegmentation provides segmentation without requiring a new architectural design.
Microsegmentation can be applied to a subset of hosts requiring a high level of scrutiny or more broadly to maximize a data center’s security posture.
3. Mitigate threats
It is imperative for modern data center infrastructure to be able to detect threats in advance and limit attacks. A single pane of glass centralized management policy helps mitigate and block unknown threats.
Automated and policy-based network segmentation and microsegmentation are necessary, and centralized security appliances are inefficient for expanding traffic flows. Hairpinning of traffic to hardware appliances at the data center edge impairs application performance, restricts scalability, increases costs, and adds latency.


Core principles of Zero Trust
With continuous verification and attestation, Zero Trust Security architectures enable the quick detection of many types of cyberattacks and often stop intrusions before they can occur. A Zero Trust model supports microsegmentation, enabling IT to segregate network resources so potential threats can be easily contained.
Comprehensive visibility
With the increased adoption of IoT, full-spectrum visibility of all devices and users on the network has become an increasingly important—and challenging—task. Without visibility, critical security controls that support a Zero Trust model are difficult to apply. Automation, AI-based machine learning, and the ability to quickly identify device types are critical.
Authenticate and authorize
Never trust and always verify. Multiple authentication methods can be used to concurrently support a variety of use cases, including multifactor authentication based on log-in times, posture checks, and others such as new user and new device.
Identity-based access control for least-privilege access
Least-privilege access based on identity allows users and devices to access just the resources needed to perform their functions—only as long as they behave consistently with their role. An access control policy limits access to resources and dynamically adjusts access when anomalous behavior is observed, or breach is suspected.
What is endpoint security?
Endpoint security guards the company’s valuable asset—data—from vulnerabilities and threats by securing network endpoints, (hardware such as desktops, laptops, tablets, and other mobile devices used to access the company’s network). There are various types of endpoint security:
- Network Access Control (NAC): uses firewalls to control endpoint device access to the network.
- Data Loss Prevention: protects files or data hacked/exfiltrated via phishing schemes or malware installed at endpoints.
- Data Classification: identifies which data in your organization is most sensitive, placing higher value on its vulnerability so that access to it can be provided accordingly.
- URL Filtering: limits the number of websites that endpoints can connect to and protects from malware.
- Cloud Perimeter Security: puts a firewall around sensitive cloud-based data and apps to limit which endpoints can access data.
- Sandboxing: sets up a virtual environment that mimics the network for the user’s endpoint to operate, limiting access to sensitive information.
Why is infrastructure security important?
Increased interconnectivity and the adoption of cloud services, microservices, and software components across different cloud platforms and at corporate network edges have made securing technology infrastructure both more complex and more important than ever. Adopting Zero Trust Security architectures is one-way enterprises can address this challenge.
At the same time, it is very important to train employees on password and credential security to protect IT infrastructure since the human element can be the weakest link in an organization’s security strategy. Infrastructure security implements data protection across an entire company technology perimeter through these four levels:
- Physical: Protecting physical infrastructure from theft, vandalism, etc. Data recovery plans incorporating offsite backups from different geographies is also part of a physical security strategy.
- Network: Monitoring incoming and outgoing network traffic—whether on-premises, in the cloud via firewall, or via multi-factor authentication (MFA)—to verify before allowing access to network resources.
- Application: Ensuring software and firmware updates are distributed and applied across the enterprise network as outdated software can contain vulnerabilities that cyberattackers can exploit to gain access to IT systems.
- Data: Protecting data protection using common enterprise endpoint security measures such as URL filtering, anti-virus tools, sandboxing, secure email gateways, endpoint detection and response (EDR) tools, and data encryption.
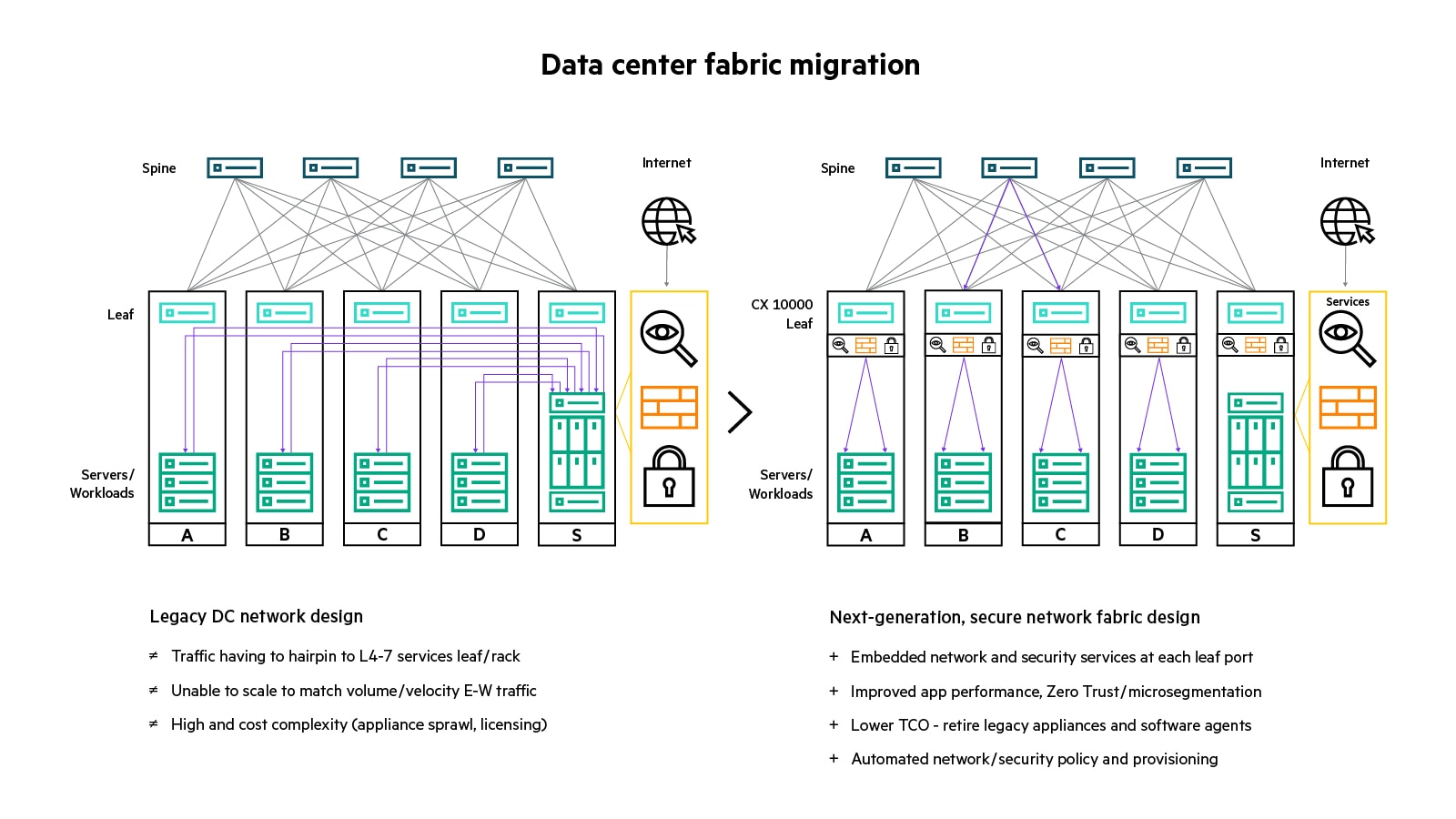
A new generation of secure data center fabrics
While data center networking has evolved over the past decade, providing higher-performing 25/100/400G leaf-spine topologies to address the volume and velocity of emerging application architectures, security and services architectures have not.
Unlike traditional perimeter security approaches, modern Zero Trust Security architectures recognize trust as a vulnerability. They assume no user, even if allowed onto the network, should be trusted by default because the user could be compromised. Identity and device attestation and authentication are required throughout the network. Every single component in the network must independently establish its trustworthiness and be authenticated by any other component it interacts with, including existing point security measures. The core principles of Zero Trust Security strategy:
- Never trust, always verify
- Assume breach
- Verify explicitly
A distributed services architecture expands Zero Trust deeper into the data center, to the network-server edge, delivering fine grained microsegmentation, dramatically scaling and strengthening the security of mission-critical workloads.
Data center fabric migration

Related products, solutions or services
Related topics
Edge-centric, cloud-enabled, and data-driven architectural solutions from HPE Aruba Networking.