Network management What is network management?
Network management is the set of processes and capabilities used to provision, configure, monitor, operate, and maintain a network. A network management system helps ensure the overall reliability, performance, and availability of the network. The widespread adoption of cloud-managed networking for scale, agility, and efficiency has given rise to a wave of innovations in network management, resulting in modern, microservices-based, cloud-native network management platforms.
Table of Contents
Time to read: 5 minutes, 25 seconds | Updated: January 27, 2026
Network management explained
Network management is a multi-functional discipline that enables IT and network operations to ensure the overall reliability, performance, and availability of the network. With digital transformation, there is also an increasing focus on the role of network management in delivering high-quality end-user experiences.
Network management typically involves the following functions outlined by the FCAPS framework:
- Fault management: Detection, isolation and issue resolution to ensure optimal network connectivity and minimize downtime due to undetected anomalies. This is also often referred to as MRT (monitoring, reporting, and troubleshooting).
- Configuration management: Deployment and provisioning of network devices such as access points, switches, and gateways, including the ongoing monitoring of devices for configuration changes.
- Accounting management: Network utilization tracking to document bandwidth consumption by users and lines of business for cost management purposes.
- Performance management: Ongoing compilation and analysis of metrics related to network performance such as response time, packet loss, and throughput to ensure acceptable service levels are maintained. Alerts are generated when acceptable thresholds are breached.
- Security management: Network authorization to ensure only authorized users and devices can access the network resources to which they have rights. Most solutions incorporate capabilities that aid firewall configuration, vulnerability management, and intrusion detection.
HPE Aruba Networking Central provides a broad set of capabilities outlined by the FCAPS network management framework to provision, configure, monitor, and troubleshoot network devices.
Why is network management important?
To maintain the health and optimal functionality of a network, complete maintenance and control across remote locations, branch, campus, data center, public, and private clouds is crucial. It enables:
- ‘Always-on’ availability for services and critical business applications through proactive issue identification and resolution, reducing downtime, and ensuring that key services are available to users.
- Enhanced security through continuous monitoring of abnormal activities and ensures secure, role-based access for devices, users, and clients, including IoT devices.
- Seamless flow of data from where it’s generated (users and IoT devices at the edge) to where it is processed. Network management tools also aid in planning and implementing improvements to accommodate growth, ensuring the network can withstand growing demand.
- Streamlined adherence to compliance commitments with applicable standards and legislation by providing monitoring and necessary documentation.
Networking-related problems have been the single biggest cause of all IT service incidents over the past three years, with half of the network problems arising due to human error
What are the key network management functions?
As outlines by the FCAPS framework, the functions constitute:
- Monitoring Network Performance: Tracking the network's performance in real-time, looking for bottlenecks, and identifying possible problems. This includes tracking bandwidth utilization, latency, packet loss, and device health.
- Configuration Management: This includes configuring routers, switches, and firewalls to meet the organization's needs. Implementing network regulations, access limitations, and quality of service characteristics are all part of this.
- Security Management: Protecting the network from cyberattacks, illegal access, and data breaches. Tasks include setting firewalls, intrusion detection systems, and maintaining compliance with security rules.
- Fault Detection and Troubleshooting: This entails determining the source of issues, such as network outages or performance deterioration, and taking remedial steps to resolve them as soon as possible.
- Capacity Planning and Scalability: Planning for the future by evaluating the network's capacity and scalability requirements. Network administrators must plan for expansion and guarantee that the network can support more users, devices, and services without degrading performance.
What are current network management challenges?
- Network Complexity: As hybrid work becomes mainstream and cloud adoption increases, traditional networks are becoming too complex to manage. Adding to this complexity is the often-independent management of WAN, wired, and wireless networks.
- Visibility: The rapid proliferation of IoT devices in support of digital transformation initiatives presents new visibility and security challenges, increasing cybersecurity risks.
- Tool Sprawl: To address a variety of workflows and functions across application, infrastructure, and cloud environments, network teams have anywhere between 4 to 15 tools on average
EMA%20Network%20Management%20Megatrends%2C%202022 . With limited interoperability, large toolsets result in a high rate of manual errors, alert fatigue, and increased downtime.
Cloud-based vs on-prem network management models
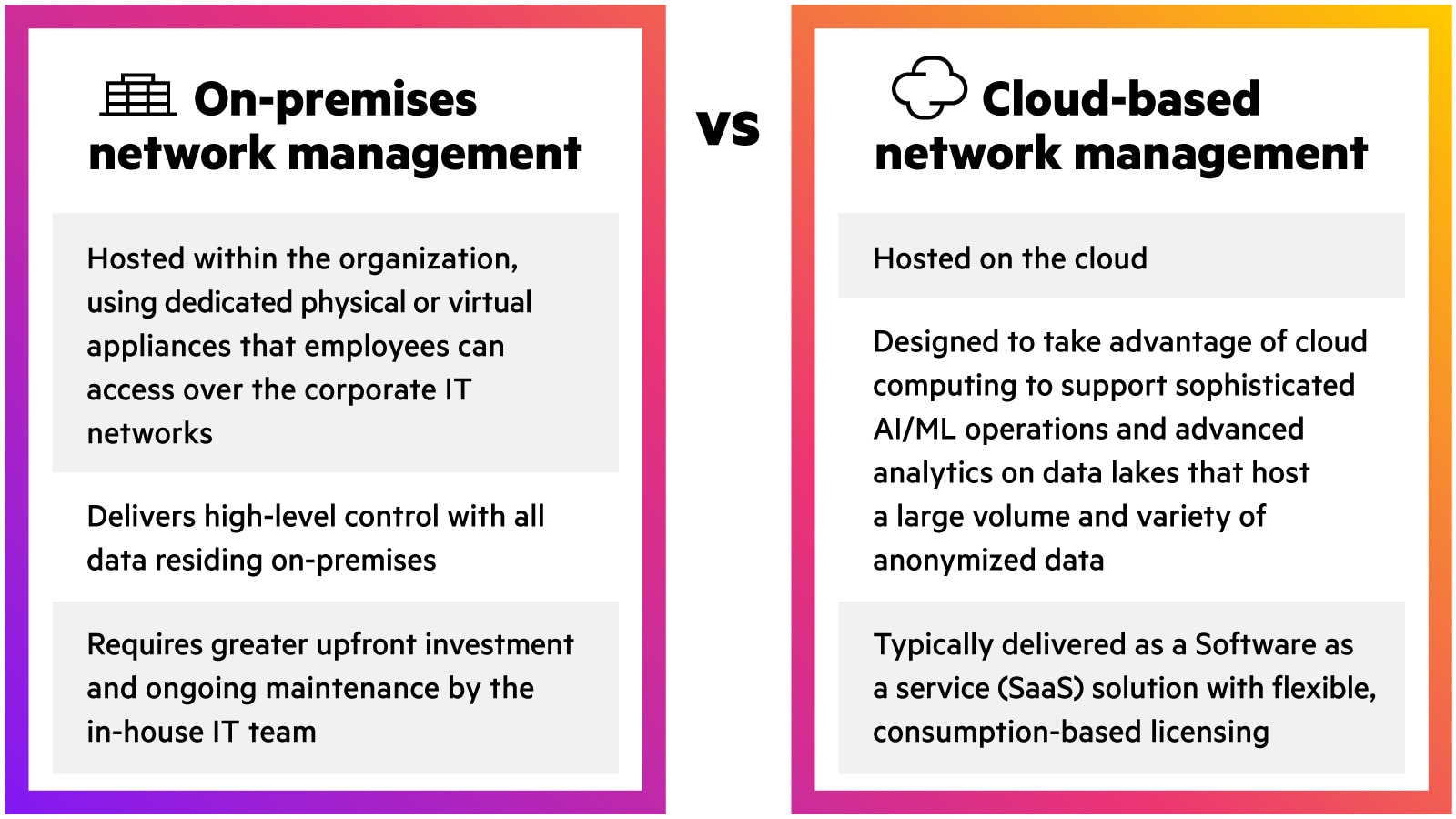

What are the benefits of cloud-based network management?
- Single point of control unifies network management across wired, wireless, and WAN networks, eliminating tool-induced management siloes to provide a single point of control and visibility.
- Scale: Scales rapidly across thousands of sites globally, without incurring CapEx for additional management hardware/appliances.
- Flexibility: Uses a modern, microservices-based architecture that provides flexibility and enables agile, automatic delivery of features without the need for planned maintenance downtime for software upgrades.
- AIOps and Analytics: Leverages data across the customer’s site and similar (anonymous) sites for AI/ML and advanced analytics, enabling anomaly detection, rapid troubleshooting, and optimization recommendations to drive operational efficiency.
- Programmability: Leverages RESTful APIs, streaming APIs, and webhooks for integration with the existing solution ecosystem.
Despite its several benefits, the cloud may not be the preferred or immediate choice always. Customers who require strict regulatory compliance, have data sovereignty mandates, or have legacy network designs can use the On-Premises that offer cloud-like agility and efficiency.
How to migrate to cloud-based network management?
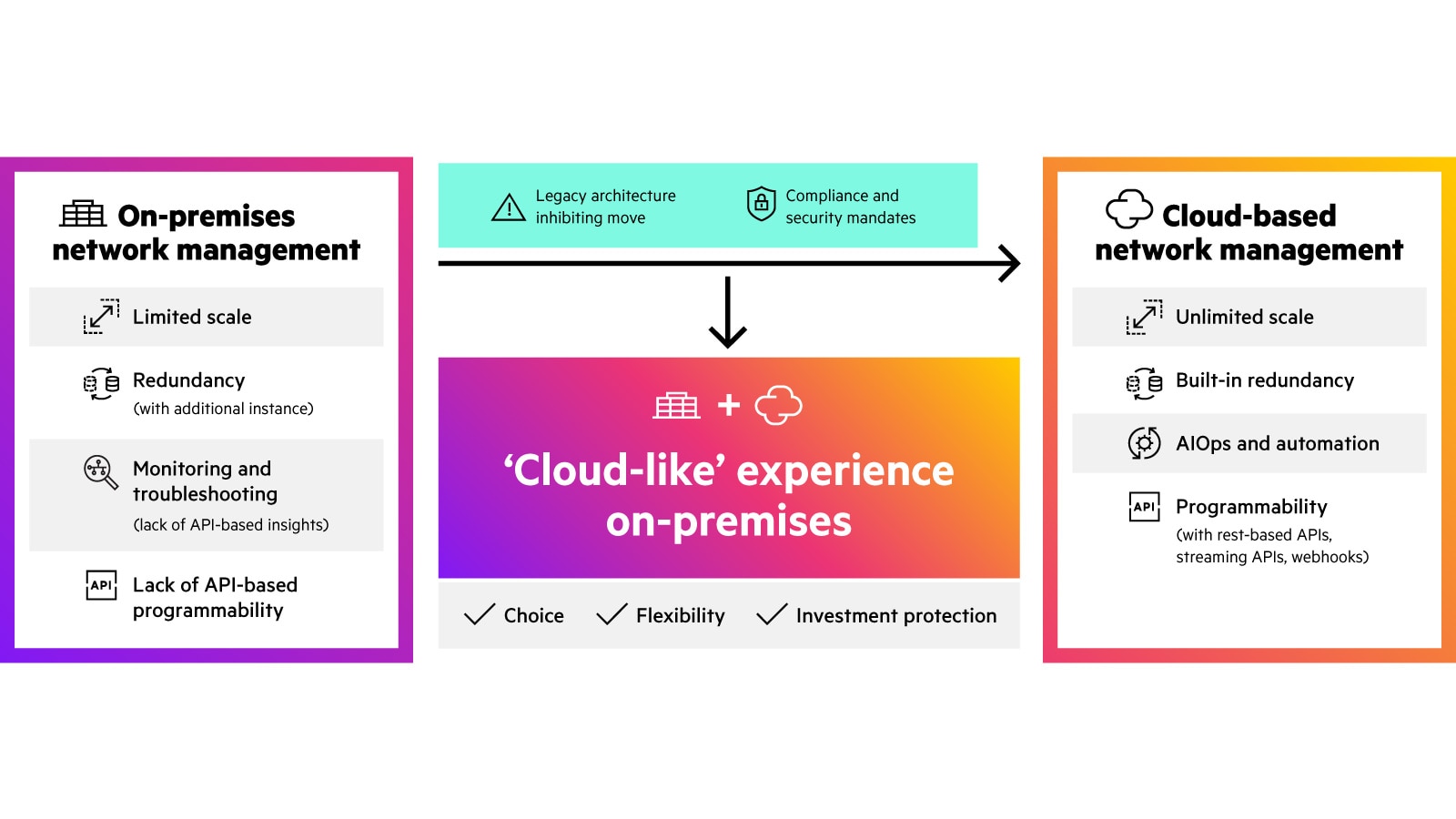

How is network management evolving?
Businesses continue to modernize their network management systems to help navigate the challenges outlined above. Key areas of innovations include:
Innovation | Description |
|---|---|
| AIOps and automation | Artificial Intelligence (AI) and Machine Learning (ML) on massive amounts of data (typically in a data lake) proactively derive insights across a range of use cases that increase network reliability, improve mean time to resolution (MTTR), and increase IT efficiency. |
| Flexible consumption | Cloud-based deployment models with support for flexible, subscription-based licensing models offers improved ROI, better financial control, and lower TCO. |
| Programmability | Microservices-based architectures with open, standards-based constructs, API support, and webhooks, enable a high degree of interoperability with other tools in the ecosystem and third-party integrations for IoT, OT, and IT convergence. |
| BYOD and IoT security | Built-in capabilities, such as AI-powered profiling, help address the inherent visibility and security challenges with BYOD and IoT, eliminating network blind spots and improving overall security posture. Security models such as Zero Trust use role-based access policies and ensure that no person or device is inherently trusted. |
| Intent-based networking | Software-defined, GUI-based workflows that automatically convert to CLI-based configurations reduce the complexity of the underlying physical network and express business intent. |
Networking management faqs
How does network management work?
Network management monitors, configures, secures, and optimizes devices and services across LAN and WAN. It collects telemetry, enforces policies, and tracks performance to ensure reliable connectivity. To drive digital transformation, it must evolve into AI-native, self-driving network solutions.
What features should I look for in network management platform?
Choose an AI-native, microservices-based platform for performance optimization. It should provide unified visibility and control across wired, wireless, and IoT, integrated security with zero trust enforcement, enterprise scale, deep observability, and a 100% open API architecture for seamless IT ecosystem integration.
What are the common challenges in network management and how are they addressed?
Executives seek to align networks with business goals, reduce costs, and prevent breaches, while operators struggle to integrate complex systems and handle constant troubleshooting. The solution: a modern network management platform with self-driving capabilities and industry-leading AIOps—designed for secure, exceptional business outcomes.
How to troubleshoot network management issues?
Modern AI-native network management should include a conversational AI assistant that answers natural language queries like “Who’s having a bad experience?” Using agentic AI, it correlates data across LAN and WAN, recommends fixes, and often resolves issues automatically—cutting MTTR and giving operators confidence in every decision.
What is the role of AI in network management?
The goal of AI in network management is to enable self-driving networks—delivering scale, fewer tickets, and faster troubleshooting. AI predicts issues before users are impacted, uses digital twins, UXI sensors, and rich telemetry to automate RCA and remediation. With permission, it can fix problems like stuck ports or non-compliant devices—true self-driving networking.