Network firewall What is a network firewall?
A network firewall is hardware or software that restricts and permits the flow of traffic between networks. Network firewalls help prevent cyberattacks by enforcing policies that block unauthorized traffic from accessing a secure network.
Table of Contents
Network firewalls explained
Network firewalls are designed to limit the flow of traffic between networks. They are often employed between a secure private network and a network with a different security posture, such as the Internet. Network firewalls can also be placed throughout a secure private network to reduce the risk of cyberattacks and prevent unauthorized access to sensitive resources.
What does a network firewall do?
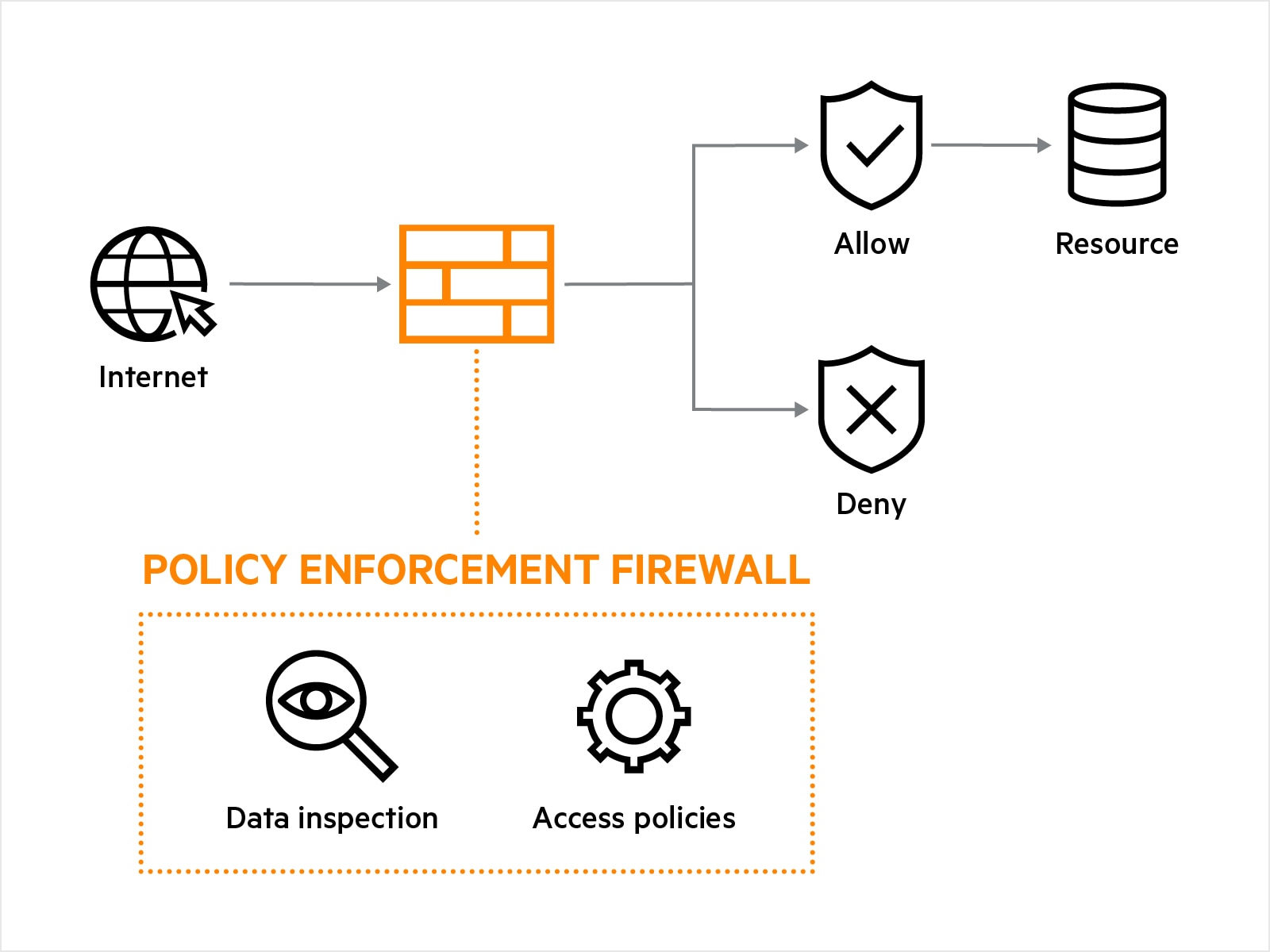
Network firewalls analyze inbound and outbound network traffic, checking for IP address, communication protocols, content type, and other traffic characteristics. After analyzing the characteristics of the traffic, the network firewall blocks or allows traffic based on established firewall policy.
Network firewall security is often required to achieve security, privacy, and compliance mandates, such as the Federal Information Security Modernization Act (FISMA) in the U.S. and the globally recognized Payment Card Industry Data Security Standard (PCI DSS).
How does a network firewall work?
Network firewalls enforce policy based on access control mechanisms. Mechanisms can be defined policies, allow/deny rulesets, and other guidelines that specify how traffic should be treated based on its characteristics.
Network firewalls examine data within the four Transmission Control Protocol/Internet Protocol (TCP/IP) communication layers: (from highest to lowest) application, transport, IP/network, and hardware/data link. TCP/IP layers guide movement of data from origin to destination. The more advanced the network firewall security technology, the more and higher order layers that can be examined. The ability to gather more information allows advanced network firewalls to provide finer traffic controls and more detailed accounting.
Which network firewall is best?
Not all network firewalls are created equal. With hybrid work, mobility, and IoT adoption on the rise, network firewalls that use rules and physical network configuration based on IP addresses are no longer adequate. The HPE Aruba Networking Policy Enforcement Firewall (PEF) provides identity-based controls to enforce application-layer security and prioritization.
PEF is a proven technology that runs on over 4 million installations worldwide. Organizations using PEF technology can implement a Zero Trust access model that uses identity, traffic attributes, and other context to centrally enforce access privileges at the time of an initial connection. Because of its technology and ability to dynamically enforce secure role-based policies, PEF has been designated a “Cyber Catalyst℠” solution by Marsh based on its ability to effectively reduce risk. Cyber Catalyst enables customers that adopt designated technologies to be considered for enhanced terms and conditions on cyber insurance policies from participating insurers.
Benefits of network firewall security
- Enforce access privileges to reduce risk. Network firewalls that only allow traffic that has been expressly permitted to pass—”deny by default”—can support Zero Trust security architectures.
- Limit access to sensitive resources. Network firewalls can prevent unauthorized users from accessing sensitive and confidential data, such as patient data and financial information.
- Protect the network from cyberthreats. Attacks caused by malware or threats propagated by malicious websites visited by users within the organization can be blocked and prevented by network firewalls.
How network firewalls work

Types of firewalls
Firewall type | What it does |
|---|---|
| Packet filtering firewall | Inspects ingress (incoming) and egress (outgoing) traffic and allows/denies passage of the traffic based on basic information like source and destination. A packet filtering firewall does not keep track of the state of incoming or outgoing traffic, and thus is also known as a stateless firewall. Due to their limitations, stateless packet filtering firewalls can be vulnerable to attacks and exploits targeting the TCP/IP stack. |
| Stateful firewall | Utilizes stateful inspection to track traffic and block traffic that deviates from expected patterns. Stateful firewalls check connections against established connections tracked in a table and can deny traffic based on rules and non-conformity with established connections. This allows stateful firewalls to protect against attacks like Distributed Denial of Service (DDoS). |
| Application firewall | Builds on statefulness capabilities with deep packet inspection functionality. Application firewalls analyze data at the application layer, comparing observed events to established patterns of activity to identify deviations and prevent threats. Application firewalls can thwart attacks carried out by unexpected commands, such as buffer overflow attacks, DoS attacks, and malware. |