MPLS What is MPLS?
MPLS, or Multiprotocol Label Switching, is a type of networking technology that is commonly used in modern-day telecommunications. MPLS is a way of routing network traffic across telecommunication networks by using labels instead of IP addresses. It can be used with any networking protocol, including Ethernet, ATM, and Frame Relay.
Table of Contents
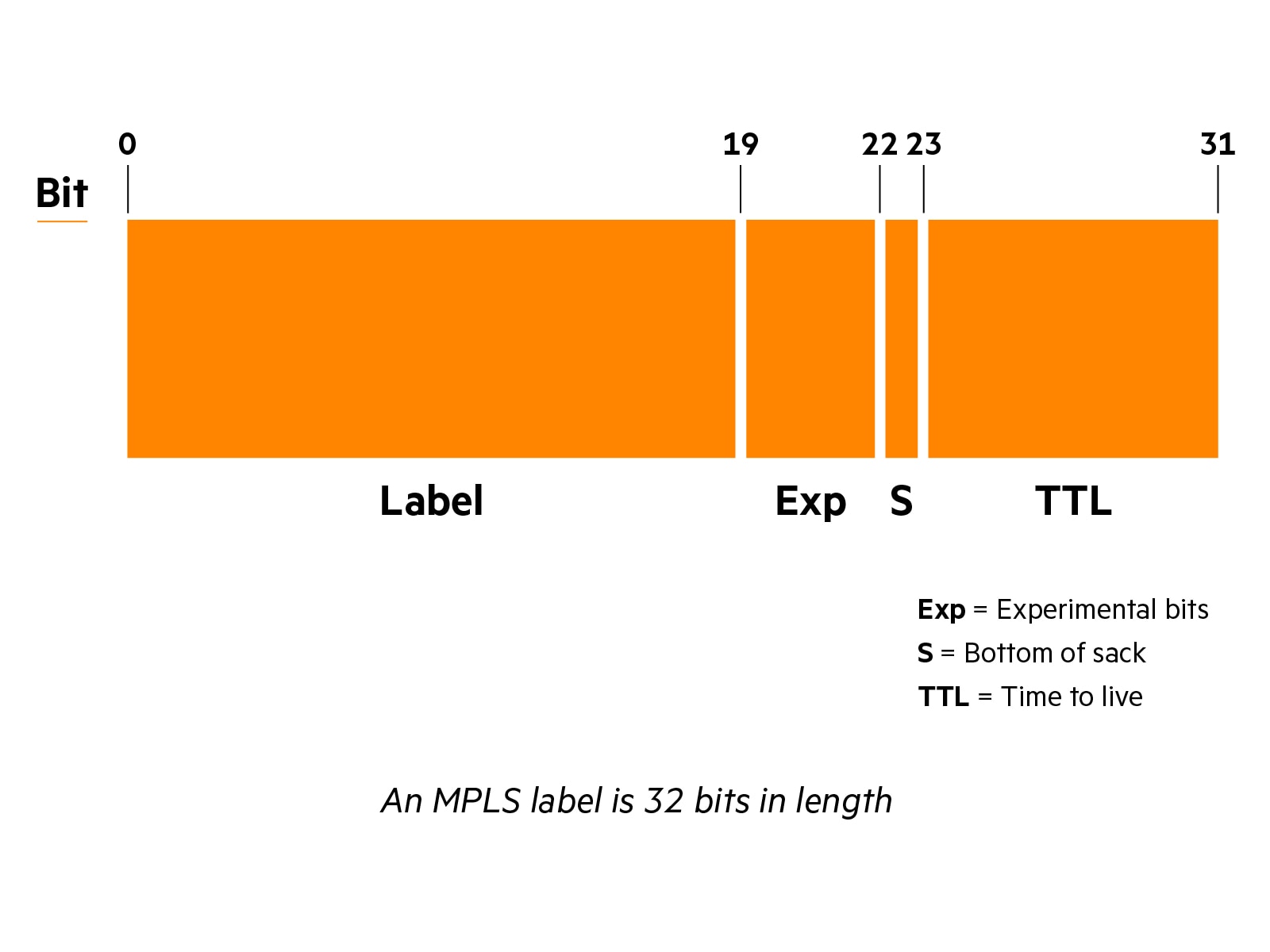

MPLS explained
MPLS was developed in the 1990s to accelerate network traffic. Unlike traditional network protocols that use source and destination addresses to route traffic, MPLS adds labels to network traffic to send packets along predetermined network paths, eliminating the need for routers to perform time-consuming route lookups for each packet and allows for faster packet forwarding.
MPLS also provides a high level of scalability as it can support large numbers of network nodes and can be used with a variety of network protocols. MPLS is often used to connect branch offices to the corporate data center. It operates at an OSI layer, often referred as layer "2.5", between layer 2 (data link layer) and layer 3 (network layer).
How does MPLS work?
Traditionally, packets are routed based on source and destination requiring routers to look up into the packet’s destination IP address and consult their routing table to forward the packet to the next hop. To eliminate this time-consuming process, MPLS works by creating virtual circuits called label-switched paths (LSPs) between two endpoints. Paths are set up based on criteria in the Forwarding Equivalent Class (FEC), describing a set of packets with similar characteristics that may be forwarded the same way.
LSPs are identified by a label attached to each MPLS packet. MPLS packets are then switched based on the label that serves as a reference point for the network to determine how to route the packet to its destination.
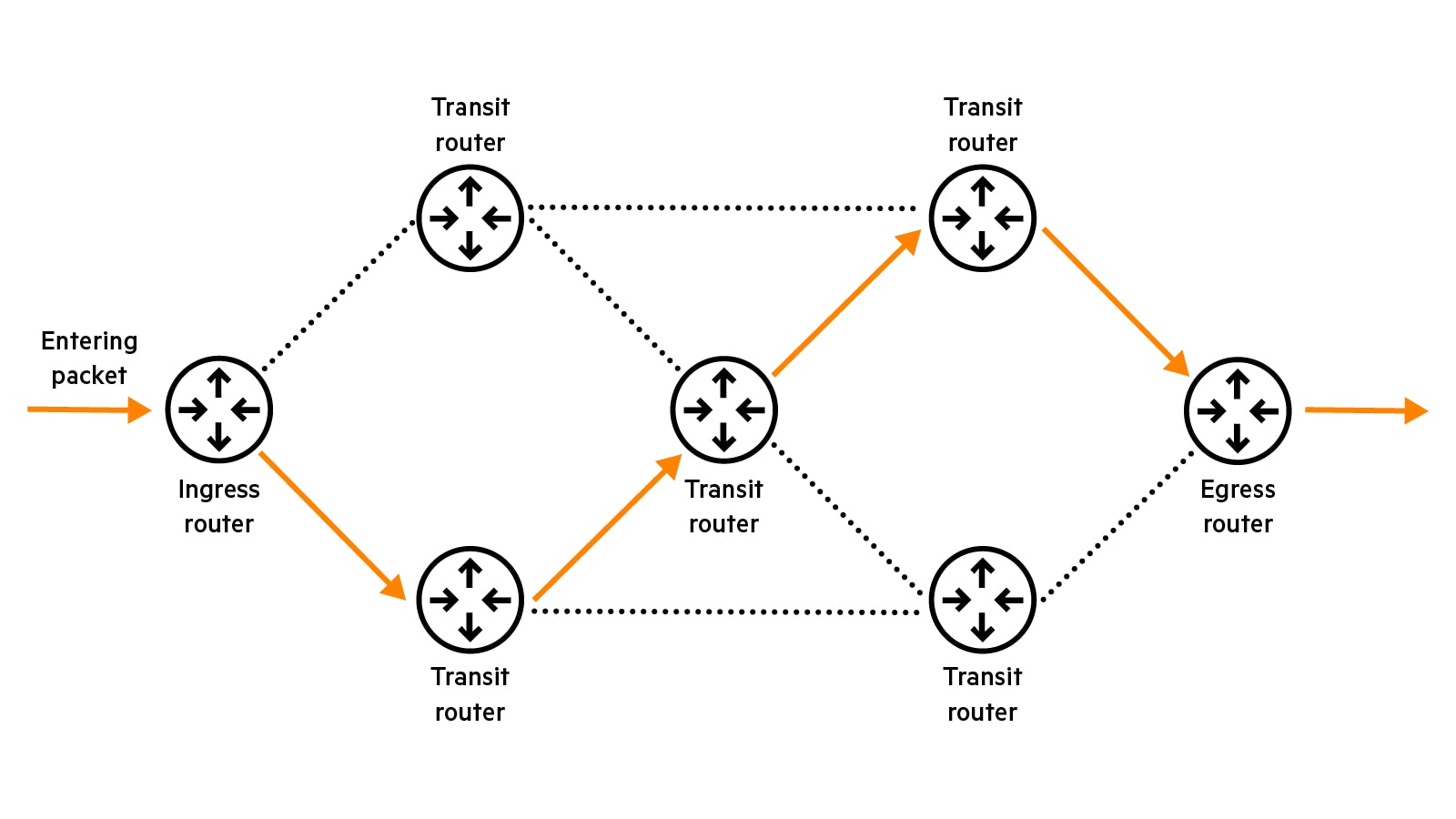
An MPLS circuit includes two types of routers: a Label Switch Router (LSR) or transit router, located in the middle of the network, and a Label Edge Router (LER) located at the edge of the network that serves as an entry point (ingress router) or as an exit point (egress router).
An MPLS router performs three types of operations:
- Push: A new label is pushed to the packet.
- Swap: The label is replaced with a new label.
- Pop: The label is removed from the packet.
As a packet enters the MPLS network, it follows these steps:
- The ingress router determines the forwarding equivalence class (FEC) for the packet and applies a label to its header.
- The transit routers in the network replace the label to forward the packet to the next router along the LSP.
- The egress router removes the label and delivers the packet to its destination.
MPLS is protocol independent as transit routers only use the information contained in the labels to forward packets. It can be used with any protocol including Ethernet, Transport over IP, ATM or Frame Relay.
Even though MPLS links are not encrypted, MPLS offers improved security compared to traditional networking technologies, providing similar security as VPN. MPLS virtual circuits are isolated from other network traffic, making it more difficult for unauthorized users to access the network.
Pros and cons of MPLS
MPLS offers several benefits over traditional networking technologies, including:
- Protocol independent: MPLS is not tied to a specific protocol. It can be used with various protocols such as Ethernet, ATM and Frame Relay.
- Business-driven: MPLS allows network administrators to define LSPs based on business needs and SLAs that prioritize certain types of traffic, such as voice and video, and over other types of traffic, such as email or file transfers.
- Scalable: MPLS is highly scalable and can be used to build large, complex networks that can support thousands of endpoints.
While MPLS offers many benefits, it also has some downsides that network administrators should be aware of:
- Rigid: Provisioning a new MPLS line can take 60 to as much as 120 days to deploy a new MPLS service at a new branch location, while broadband internet services can usually be provisioned within a few days. Additionally, enterprises are increasingly distributed making it difficult to install an MPLS line at each location.
- Expensive: MPLS can be expensive, particularly for small organizations that do not require high-performance networks. The growing demand for greater bandwidth and connectivity speed, especially with the growing use of voice and video applications, often makes MPLS circuits too expensive to scale for organizations.
- Cloud application performance: In traditional network architectures based on MPLS, IT administrators must backhaul SaaS application traffic to the data center for security inspection, significantly impacting application performance, while it is more efficient to route SaaS traffic to the cloud directly from branch locations.
MPLS vs SD‑WAN
When MPLS was first developed, it offered many advantages over traditional networks. However, in the digital age, MPLS fails to provide the flexibility and security needed by modern cloud architectures and hybrid workers. Due to the increasing demand for bandwidth and high cost of bandwidth, many organizations have difficulty to maintain a high level of service in branch offices with MPLS networks. Additionally, moving business-critical applications to the cloud creates bottlenecks as internet traffic must be routed back to the data center for security inspection.
By virtualizing network connections, an SD‑WAN can bond multiple links including MPLS, broadband internet and 5G, and increase network bandwidth. SD‑WAN uses encrypted IPsec tunnels across the entire fabric, securing data in transit. The solution also monitors network conditions in real time and quickly adapt. If a brownout or blackout occurs, it automatically switches to the remaining links increasing reliability.
An advanced SD‑WAN can even replace legacy MPLS lines with broadband internet, and reduce costs, by mitigating the effects of jitter and packet loss found in broadband links. This is done by automatically rebuilding lost packets with FEC (Forward Error Correction). The solution can also overcome latency effects due to geographical distance with WAN optimization through TCP protocol acceleration and data reduction techniques.
SD‑WAN supports cloud architectures by automatically breaking out the internet traffic through application first packet identification, eliminating the need to backhaul the internet traffic to the corporate data center. Trusted SaaS traffic is sent directly to the cloud while untrusted traffic is directed to cloud security services (Security Service Edge or SSE) in a SASE architecture. Virtual instances of SD‑WAN can also be deployed directly to cloud providers such as AWS, Microsoft Azure and Google Cloud, creating a bookended solution from edge to cloud, providing predictable application performance. Finally, an advanced SD‑WAN offers various features in addition to SD‑WAN, such as an integrated router, next-generation firewall and WAN optimization allowing organizations to retire their legacy equipment in branch offices. An advanced SD‑WAN is centrally orchestrated so that networking and security policies are automatically configured and updated in minutes through zero touch provisioning, greatly simplifying operations.